Vulnerability Assessment and Penetration Testing Services (VPAT) | Accredify Global
Introduction: Understanding What is VAPT and its Significance in Cybersecurity
In today’s digital age, cybersecurity has become a critical concern for organizations across various industries. With the increasing number of cyber threats and data breaches, it has become imperative for businesses to adopt robust measures to safeguard their sensitive information. One such essential practice is VAPT full form is Vulnerability Assessment and Penetration Testing , a process that plays a crucial role in ensuring the security of an organization’s IT infrastructure.
VAPT involves identifying vulnerabilities in an organization’s systems, networks, and applications through comprehensive assessments. These assessments are performed by skilled cybersecurity professionals who simulate real-world attacks to identify potential weaknesses that malicious actors could exploit. By conducting VAPT, organizations can proactively address these vulnerabilities before they can be exploited by cybercriminals.
The significance of VAPT cannot be underestimated in the realm of cybersecurity. It provides organizations with valuable insights into their security posture and helps them identify areas that require immediate attention. Moreover, VAPT is often mandated by regulatory bodies and industry standards such as ISO 27001 compliance, making it an essential component for businesses striving to maintain data integrity and protect customer trust.
A VAPT report is a comprehensive examination of the vulnerabilities found during the security test.
In this section, we will delve deeper into the concept of VAPT and explore its meaning and significance in securing IT infrastructures against evolving cyber threats. We will also discuss various use cases and best practices related to VAPT implementation within organizations.
Which of the following is Best Used with Vulnerability Assessments?
White box testingThe Vapt test fully comprehends the system’s functionality, including its source code, documents, internal structures, and workflow. Because of this transparency, tests can be run much more quickly, and the results can be thoroughly analyzed.
Black box testingThe tester in this instance is unaware of the functionality, codes, architecture, and structures. The tester simulates a hostile incursion and evaluates the system’s reactions to imitate real malicious attacks.
Gray box testingGray box testing strikes a balance between the two by giving the tester some knowledge about the application. The goal is to find configuration-related issues.
Who Needs CMMI Certification?
- 🖥️ IT & SaaS Companies – Protects software applications and cloud platforms.
- 🏦 Financial Institutions & Banks – Ensures secure transactions and regulatory compliance.
- 🛒 E-Commerce Businesses – Prevents fraud, data breaches, and online threats.
- 🏥 Healthcare Providers – Secures patient data and meets HIPAA compliance.
- ☁️ Cloud Service Providers – Strengthens cloud security and access controls.
Key Modules of VAPT Certification
1. Vulnerability Assessment (VA)
- ✔ Identifies security weaknesses in networks, applications, and infrastructure.
- ✔ Automates scanning to detect known vulnerabilities and misconfigurations.
- ✔ Provides detailed reports with risk classifications and remediation guidance.
2. Penetration Testing (PT)
- ✔ Simulates real-world cyberattacks to evaluate security resilience.
- ✔ Uses ethical hacking techniques to test network, web, and mobile applications.
- ✔ Uncovers zero-day vulnerabilities and security loopholes.
3. Risk Assessment & Threat Analysis
- ✔ Identifies critical business assets and evaluates potential attack vectors.
- ✔ Analyzes threats based on impact, likelihood, and exploitability.
- ✔ Implements proactive security measures to mitigate risks.
4. Compliance & Regulatory Alignment
- ✔ Aligns security controls with ISO 27001, NIST, GDPR, HIPAA, and PCI-DSS.
- ✔ Ensures industry-wide compliance for financial, healthcare, IT, and cloud providers.
- ✔ Provides detailed audit reports for regulatory compliance.
5. Continuous Monitoring & Security Hardening
- ✔ Conducts periodic security assessments to stay ahead of evolving threats.
- ✔ Implements security patches, updates, and best practices.
- ✔ Strengthens firewalls, encryption, and access controls.
Services
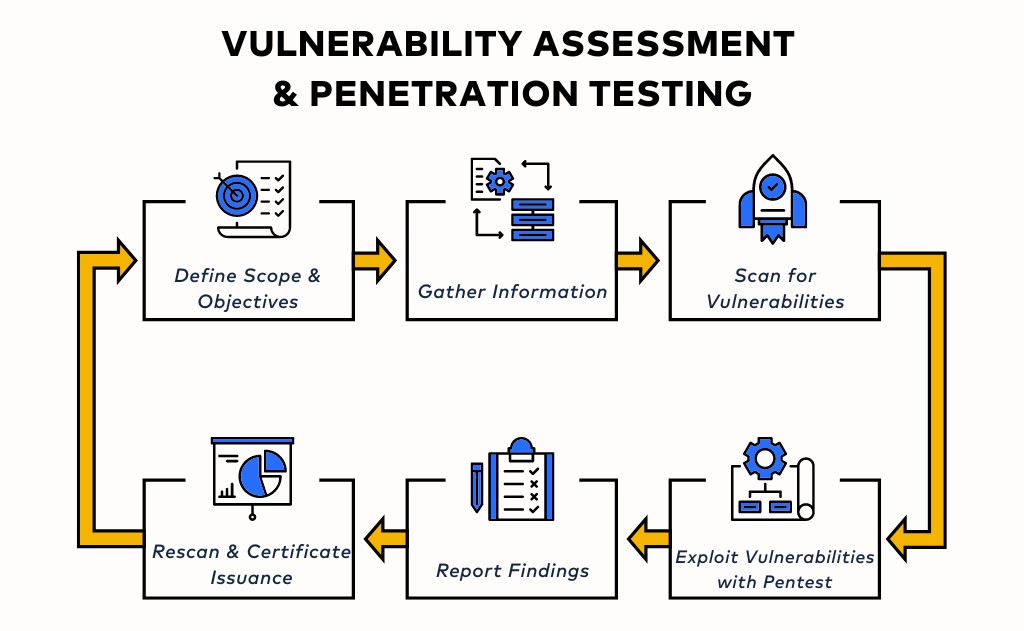
Why Vulnerability Assessment and Penetration Testing (VAPT) is Crucial for IT Industries?
Data breaches and cyber threats are becoming increasingly prevalent, Information Technologies Industries must prioritize vulnerability assessment and penetration testing (VAPT) as part of their security measures.
Vulnerability assessment involves identifying potential weaknesses in a network or system that could be exploited by hackers. By conducting regular assessments, IT industries can proactively identify and address vulnerabilities before they are exploited, thus minimizing the risk of data breaches and unauthorized access.
Penetration testing takes the assessment a step further by simulating real-world attacks to evaluate the effectiveness of existing security controls. This process helps identify any gaps in network security, allowing organizations to strengthen their defenses and mitigate potential risks.
Implementing VAPT not only protects sensitive data but also safeguards an organization’s reputation. A single data breach can have severe consequences, including financial loss, damage to brand reputation, and legal implications. By investing in comprehensive IT security assessments, companies demonstrate their commitment to protecting customer information and maintaining trust.
Furthermore, compliance with industry regulations such as GDPR (General Data Protection Regulation), ISO 27001, CMMI, SOC-1 and SOC-2 often requires organizations to conduct regular VAPT assessments. Failure to comply with these regulations can result in hefty fines and legal penalties.
Benefits of VAPT testing in IT Industries:-
In the subject of cybersecurity, particularly within IT enterprises, vulnerability assessment and penetration testing (VAPT) are crucial elements. Here are some key benefits:
- ✅ Identifying Weaknesses: VAPT assists enterprises in identifying vulnerabilities in their systems, networks, and applications Before attackers do, this proactive approach enables the quick repair or mitigation of these weaknesses.
- ✅ Risk Assessment: VAPT offers a thorough evaluation of the possible effects that exploits might have on the system. By concentrating on high-risk vulnerabilities, it can help prioritize security efforts.
- ✅ Regulatory Compliance: The periodic VAPT is mandated by laws in several businesses. Through the execution of these tests, organizations can comply with legal obligations, avoid penalties, and showcase to stakeholders their commitment to security.
- ✅ Preventing Financial Loss: Due to data breaches, ransomware attacks, etc., cyberattacks can cause substantial financial loss. Such situations can be avoided through VAPT, protecting the company from significant financial loss.
- ✅ Protecting Customer Trust: Businesses may keep their customers’ trust by guaranteeing the security of their systems. A secure business is more likely to keep its clients and lure in new ones.
- ✅ Creating Security Awareness: Additionally, VAPT aids in instructing the organization’s workforce about the significance of security precautions and how to react in the event of a breach.
- ✅ Enhancing Business Continuity: Businesses can avoid disruptions brought on by cyberattacks, ensuring smooth operations and business continuity, by discovering and addressing vulnerabilities.
- ✅ Informed Decision Making: The thorough reports produced by VAPT offer insightful information that helps guide decisions regarding IT investments and security protocols.
Since new vulnerabilities might develop over time as technology and threat landscapes change, VAPT should be a continuous process rather than a one-time occurrence.
PDCA Cycle | Accredify Global
- Plan – to think that what do we need to achieve in our organization
- Do – to execute a planned action which will help us achieve the required objective
- Check – monitor against the standards) (policies, objectives, requirements)
- Action – finally implementing what has been rechecked.
ISO CERTIFICATION. 3 STEPS. 30 DAYS. DONE !! | ACCREDIFY GLOBAL
Accredify Global, we follow a structured and transparent ISO certification process to help businesses achieve international compliance efficiently. Our streamlined approach ensures a hassle-free experience from initial consultation to final certification..
3. Audit Review & Certification
- Objective: Validate your management system through an external audit and achieve certification.
- Actions:
- Conduct an internal audit to ensure readiness for the certification audit, utilizing Accredify Global's auditing tools and resources.
- Schedule and undergo an external audit with Accredify Global's accredited certification body.
- Address any non-conformities identified during the audit with support from Accredify Global's consultants.
- Outcome: Successful certification and ongoing compliance with the ISO standard, with continuous support and guidance from Accredify Global.
